
Smarter, Faster, Safer: The Role of Graph Databases in Airport Custom Security

Custom inspections at airports are one thing you can never avoid for security reasons. Though this may be a long and bothersome process for many, it's a vital step in ensuring the safety and legality of imported goods in every country. But why does the process take so long in almost every airport? This article covers the logistical challenges posed to every customs inspection due to the sheer volume of passengers and their belongings and explores possible solutions using Graph Database technology.
Efforts in the past
While efforts were made to streamline this process and reduce customs passage times, ingenious smuggling techniques continued to outsmart the system, evading tariffs and reporting requirements. One prevalent method experimented with in the past involved using fellow travelers as proxies to bypass stringent checks. While a comprehensive inspection might deter such illegal activities, it proved impractical due to the time it consumed and the inconvenience it posed to all passengers.
Challenges
Let's break down the challenges posed in this technical, logistical operation. Customs inspection faced several challenges, including the analysis of the relationship between smugglers and their associates:
-
Multiple travelers under one reservation
While it is relatively straightforward to scrutinize travelers entering the country under the same reservation number, the task becomes significantly more complex when dealing with individuals concealed under different reservation numbers. -
High crime area with a short travel distance
Detecting smugglers operating within short-distance flights often involves an insufficient amount of time allocated for the analysis, especially in high-crime areas.
The potential solution to surmount these limitations was considered data-driven network association analysis. The system identifies potential accomplices swiftly and accurately by assessing the connections between smugglers and their collaborators while concurrently managing the performance of existing analysis systems.
Solutions using deep-analysis of big data
To identify smugglers and their associates, a Graph-based deep-analysis platform can be utilized. The database can construct a comprehensive graph representation of the target network, depicting smugglers and their associates as 'nodes' and illustrating their connections as 'edges' within the graph model. This graphical approach offers a streamlined means to traverse intricate network structures, facilitating the identification of potentially concealed smugglers and their companions.
1. Integrated analytical system
This specialized database stores diverse traveler information gathered from expansive data platforms in a structured graph format, allowing real-time analysis of travel companions. Within this system, potential smugglers are precisely categorized, and they are efficiently identified from among travelers.
Definition of risk companion (F.A.C.T Analysis)
-
Fellow Traveler: Someone who travels with potential smuggler (on the same flight)
-
AcquaintanceL Accomplice of potential smugglers (in the same group that booked the same flight or had frequent trips on the same flight in the past)
-
Conspirator: Co-conspirators (in the same group that booked the same flight or had frequent trips on the same flight in the past)
-
Trafficker: Smugglers (brought prohibited or unreported goods without customs declaration report)
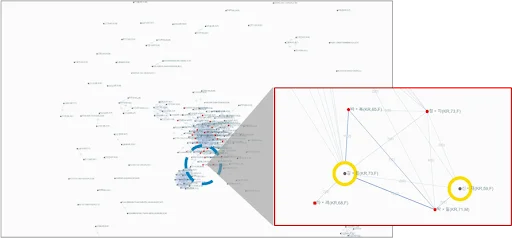
Figure 1. Detection of Relationship Between Offender and Hidden Companion
[Node - Name (nationality, age, gender),
Edge - Number of flights (number of group reservations)]
2. PostgreSQL Compatibility
The AGEDB graph database seamlessly integrates with relational databases, particularly PostgreSQL, through its extension that enhances it with powerful graph capabilities. This compatibility empowers airports to effortlessly incorporate unstructured data into their existing database systems. Additionally, AGEDB's graph-as-an-extension model facilitates straightforward data visualization, allowing efficient storage, management, and analysis of diverse data within a graph structure.
Our graph database offers real-time, user-friendly traveler pattern analysis on the dashboard. By integrating this extension with the historical data existing in the relational databases, it also helps uncover hidden patterns and connections among smugglers and their companions, streamlining the decision-making process.
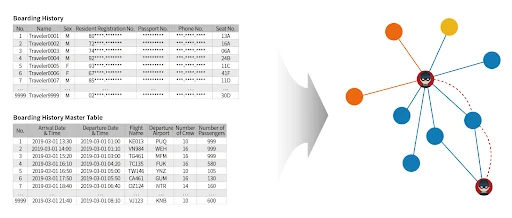
Figure 2. Graph Modeling Concept
Conclusion
In conclusion, the challenges faced by customs inspections at airports are undeniable, given the need for security and the ever-increasing volume of travelers. The traditional methods often fell short in dealing with the complexity of identifying smugglers and their associates, resulting in inconvenience for all passengers. However, with the advent of Graph Database technology and data-driven network association analysis, a new era in customs inspection has dawned.
By constructing a comprehensive graph representation of traveler networks and categorizing potential smugglers and their companions, this technology offers a streamlined solution. The deep analysis of big data, integrated analytical systems, and PostgreSQL compatibility make it possible to swiftly and accurately identify concealed smugglers and their collaborators. Through this innovative approach, airports can enhance security, expedite customs processes, and ensure the safety and legality of imported goods. Customs inspections may always be a necessary inconvenience, but with Graph Database technology, we're taking a significant step towards a safer and more efficient future in airport security.
If you are interested in applying these technologies in your field, contact us today to learn more about applications in different industries and to get a head-start on a new deep-analysis to combat potential frauds!